5. Virtual Networks
VNet Overview
What are VNets? - Vnets are private isolated hosting enviromnents.
 Implementation -
Implementation -
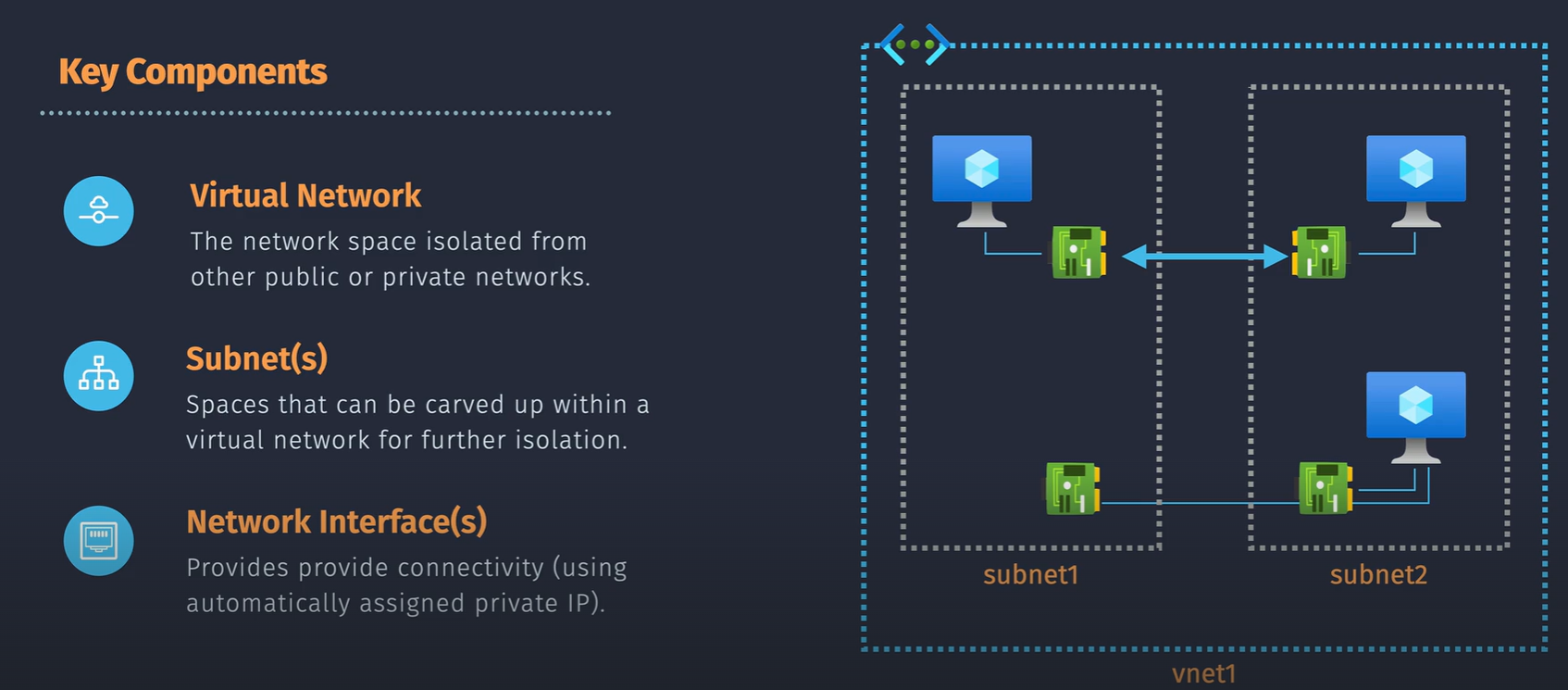
- VNet
- Subnet
- Network interfaces
Virtual network exists in a region and spans all availability zones in a region.
What this looks like:
 How to configure:
How to configure:
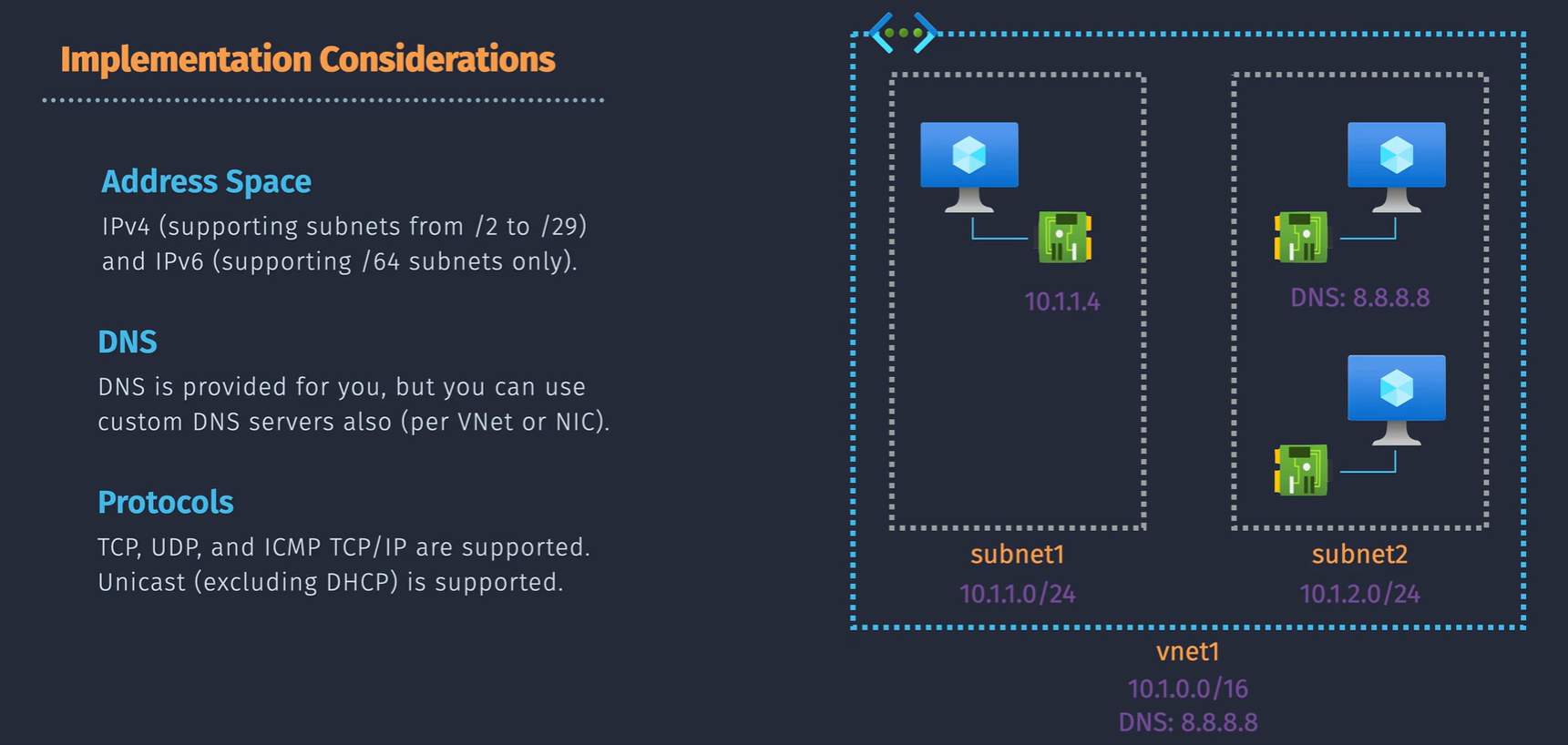
- need an address space - CIDR notation - /16 on the vnet gives us the ability to give us /24 subnets
- DNS is provided for you inside of the vnet - can select custom DNS such as 8.8.8.8 for Google if you'd like to.
- protocols, TCP, UDP ICMP TCP/IP
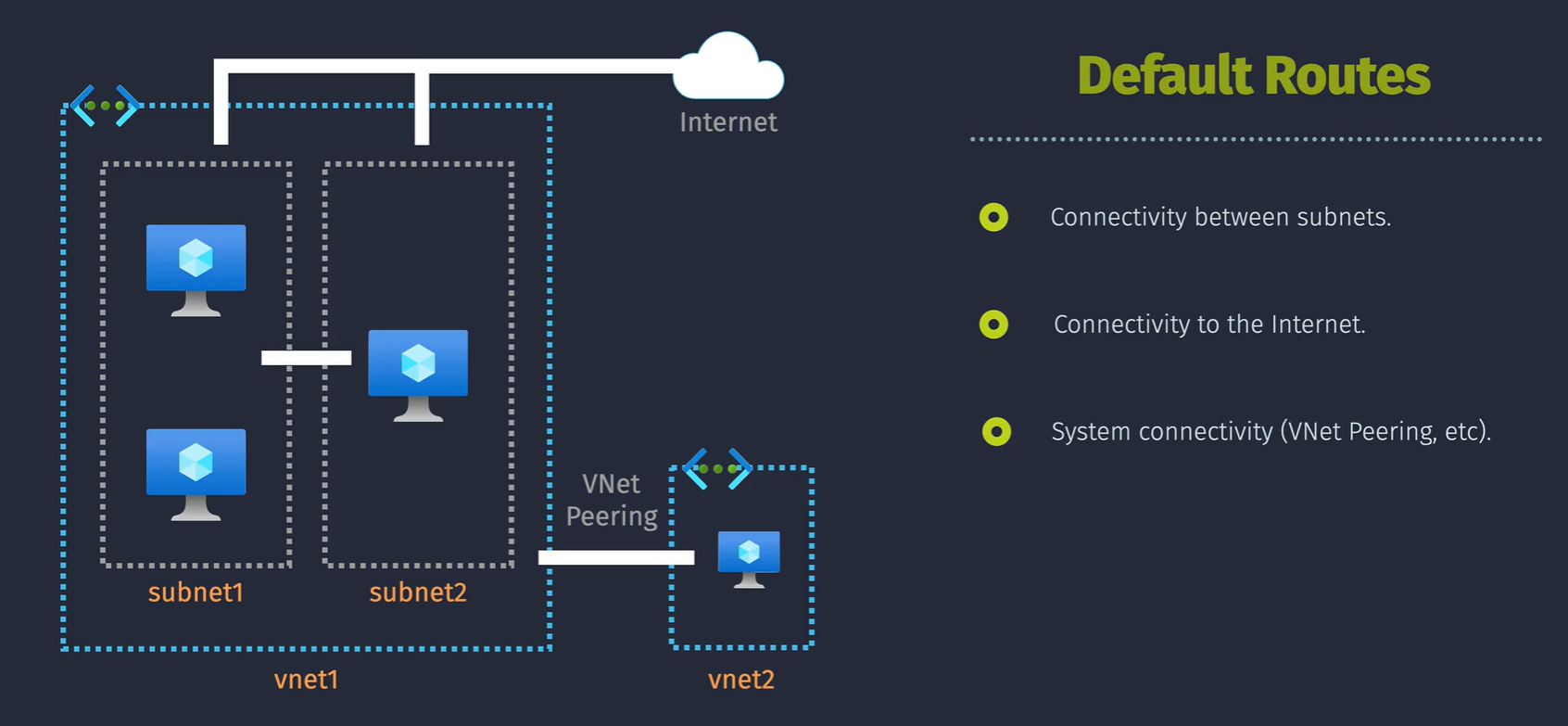
What do we get by default?
- connectivity between subnets - sn1 can talk to sn2 and sn3.
- connectivity out to the Public Internet
- system connectivity - VNet peering - connecting to other VNets.
Demo - Create a VNet
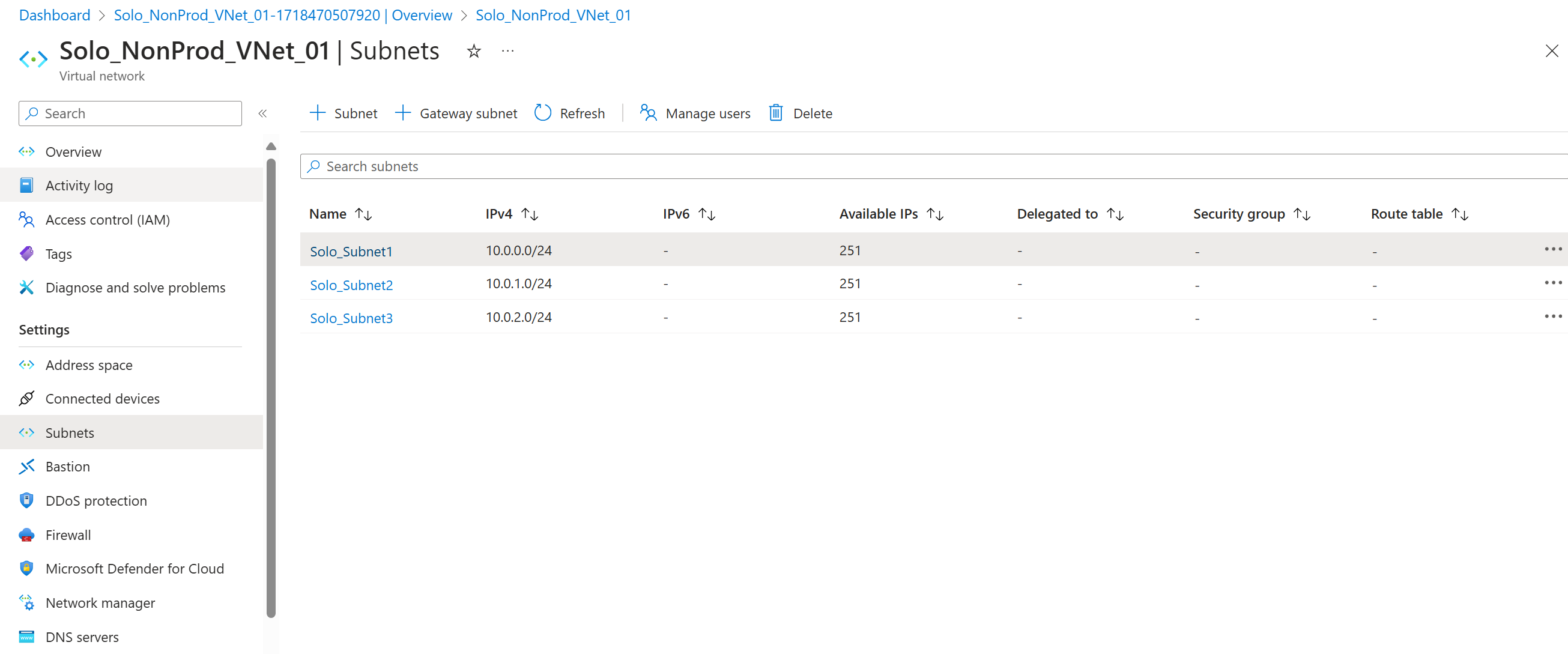 Subnet address range must be within the VNet IP range.
You cannot enable IPv6 on a subnet where IPv6 is not configured on the VNet.
Subnet address range must be within the VNet IP range.
You cannot enable IPv6 on a subnet where IPv6 is not configured on the VNet.
IP Addressing
- Private IP
- Public IP
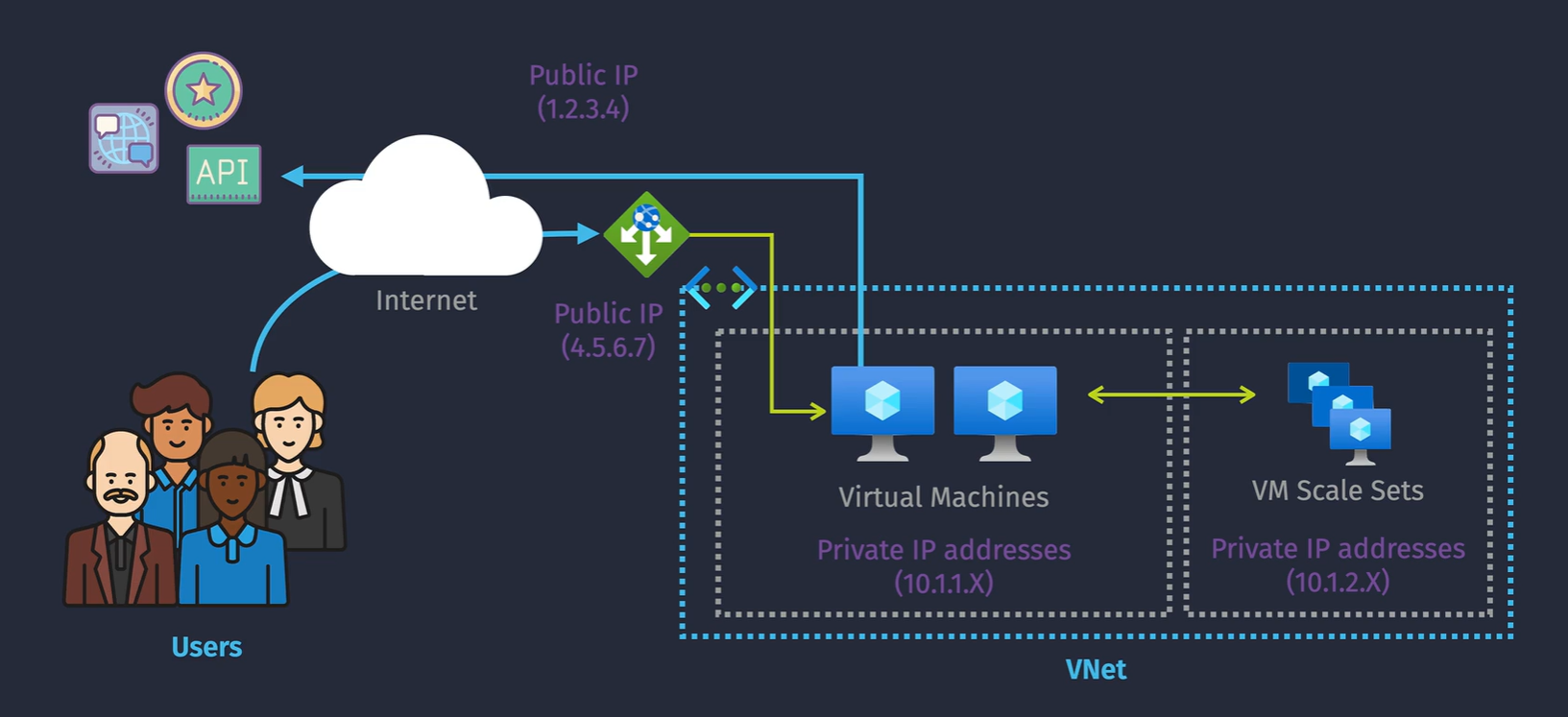
Private IP addressing
- Works by association -
- IPs are allocated either dynamically or static, but you can't reserve the addresses in advance. You can create the resource, create the interface and then assign the IP to the interface
Considerations:
- cannot allocate the first 4 or the last IP's in a subnet.
Public IP
Need to create a standalone resource and then associate that resource to your interface.
- basic (deprecating)
- standard
Can be dynamic or static
- if you need a range of IP addresses, assign a
Public IP Prefixwhich assigns IP's from a pool - bring your own IP is also an option.
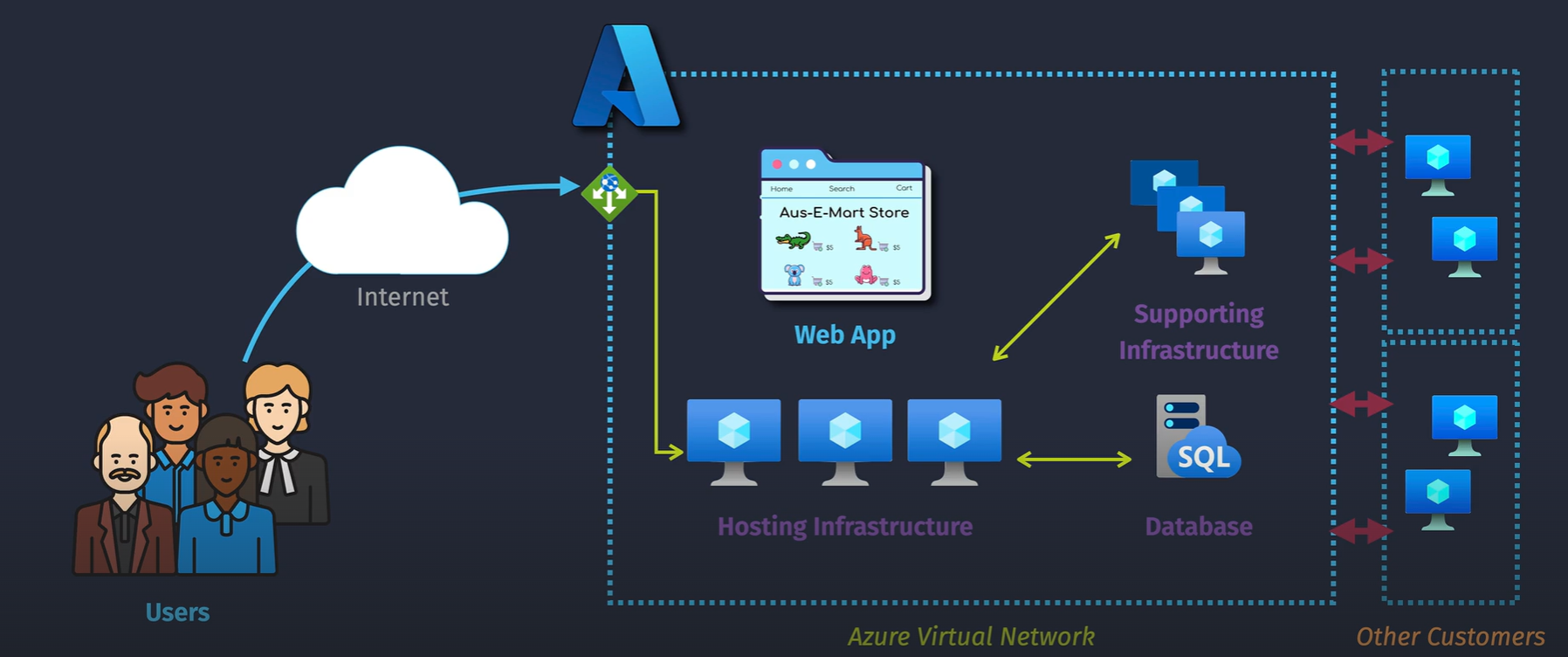
Outbound connectivity
- Internet by default
- if no IP is configured, MS will give you a public IP
- public load balancer SNAT - can be routed out via the pubilc IP of a load balancer.
- NAT Gateway - provides connectivity outbound via private IP conversion to Public IP
Public services
Some services are public by design, such as SQL
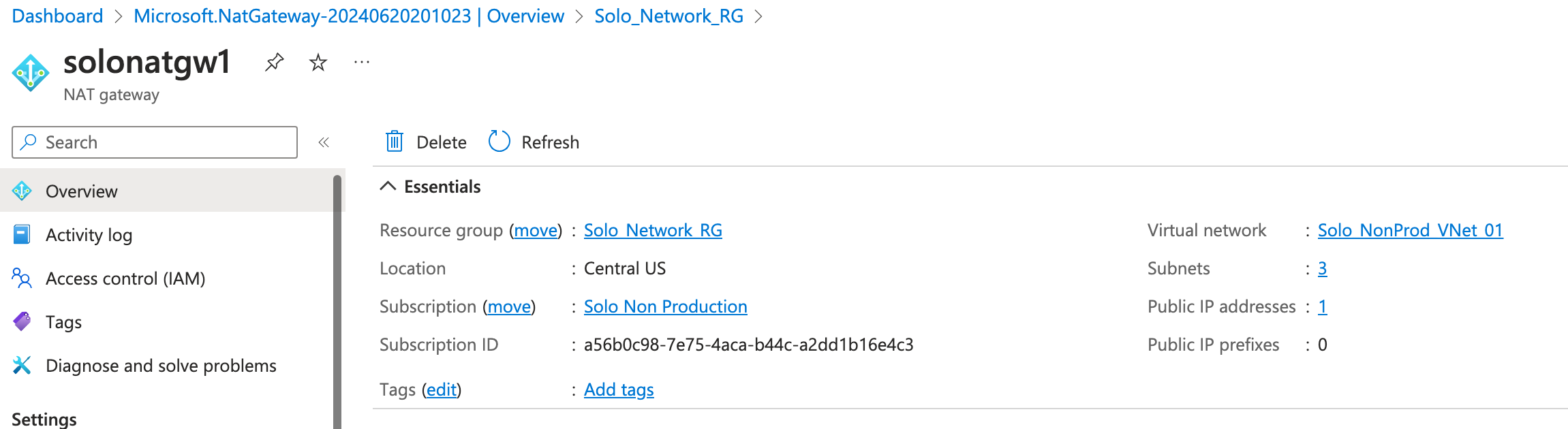
Demo - Create a NAT gateway
- Create a public IP - standard
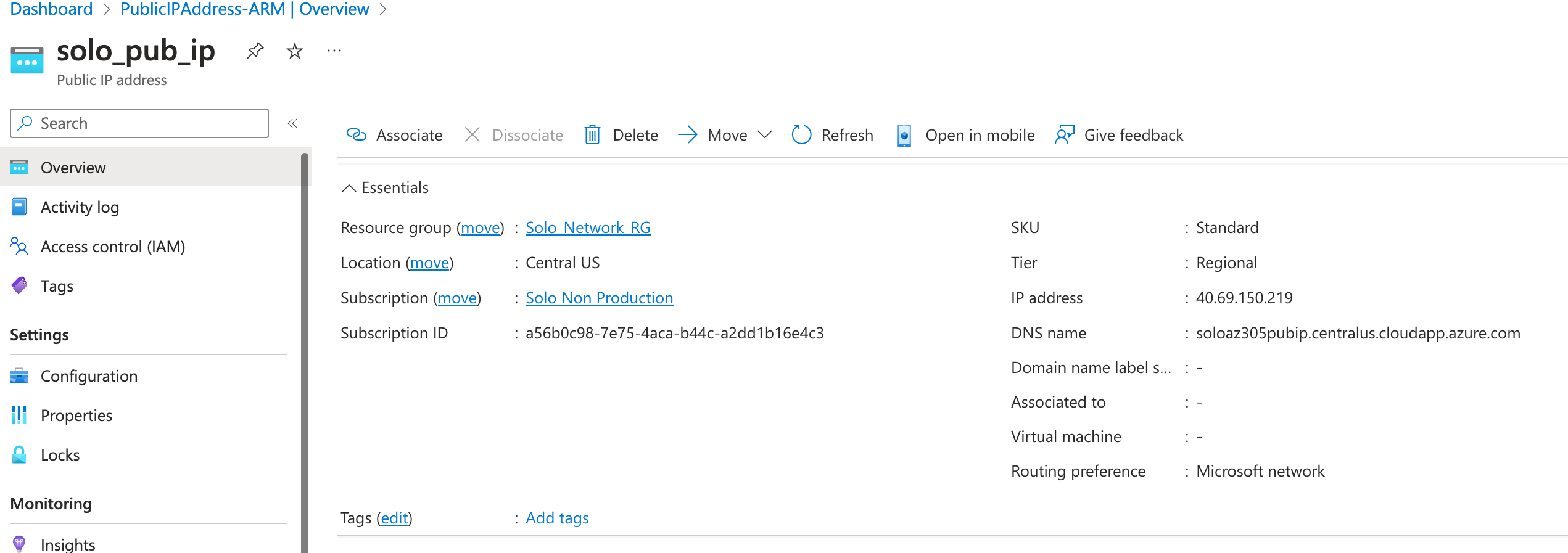
- Create a NAT Gateway for a VNet.
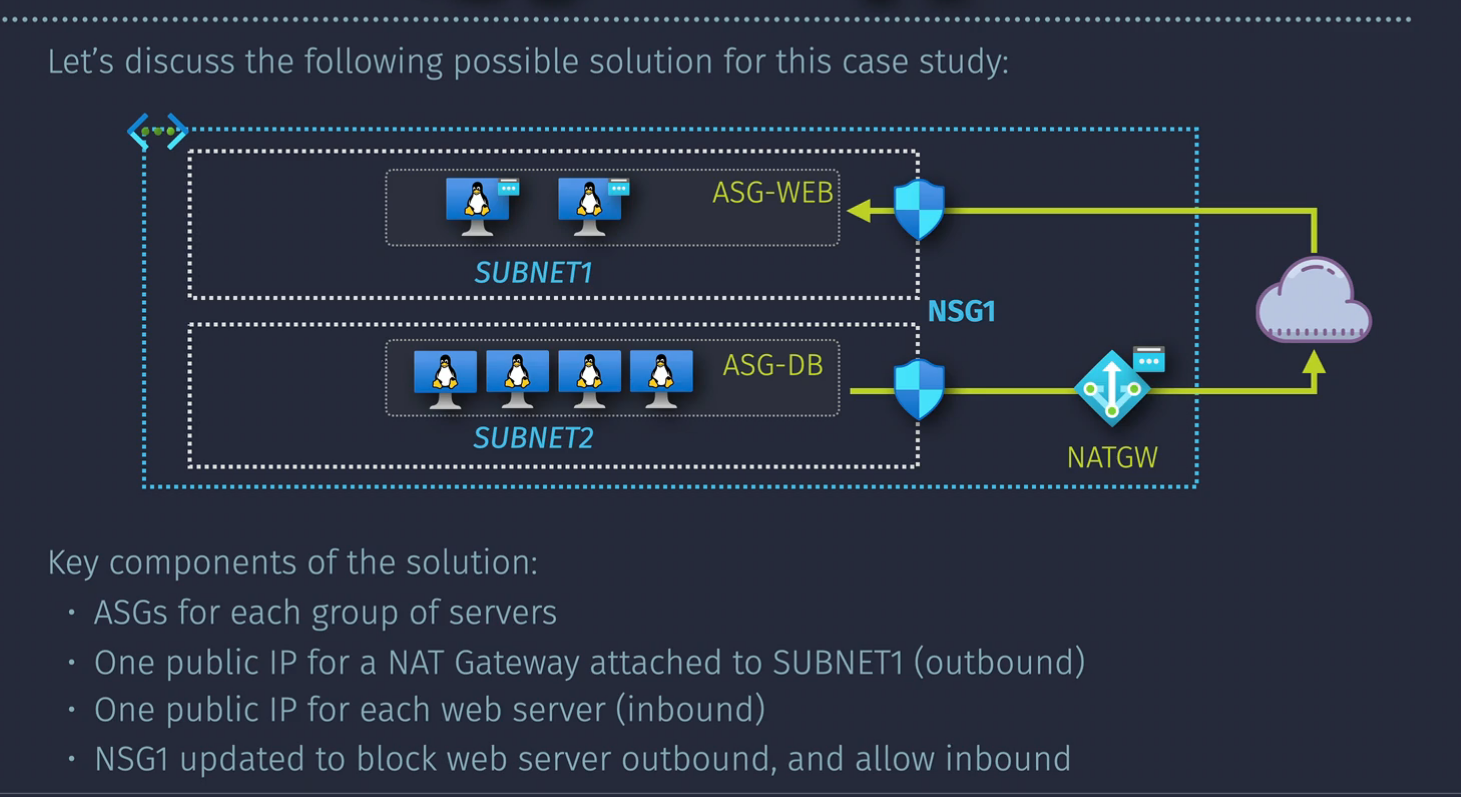
Network Security Groups
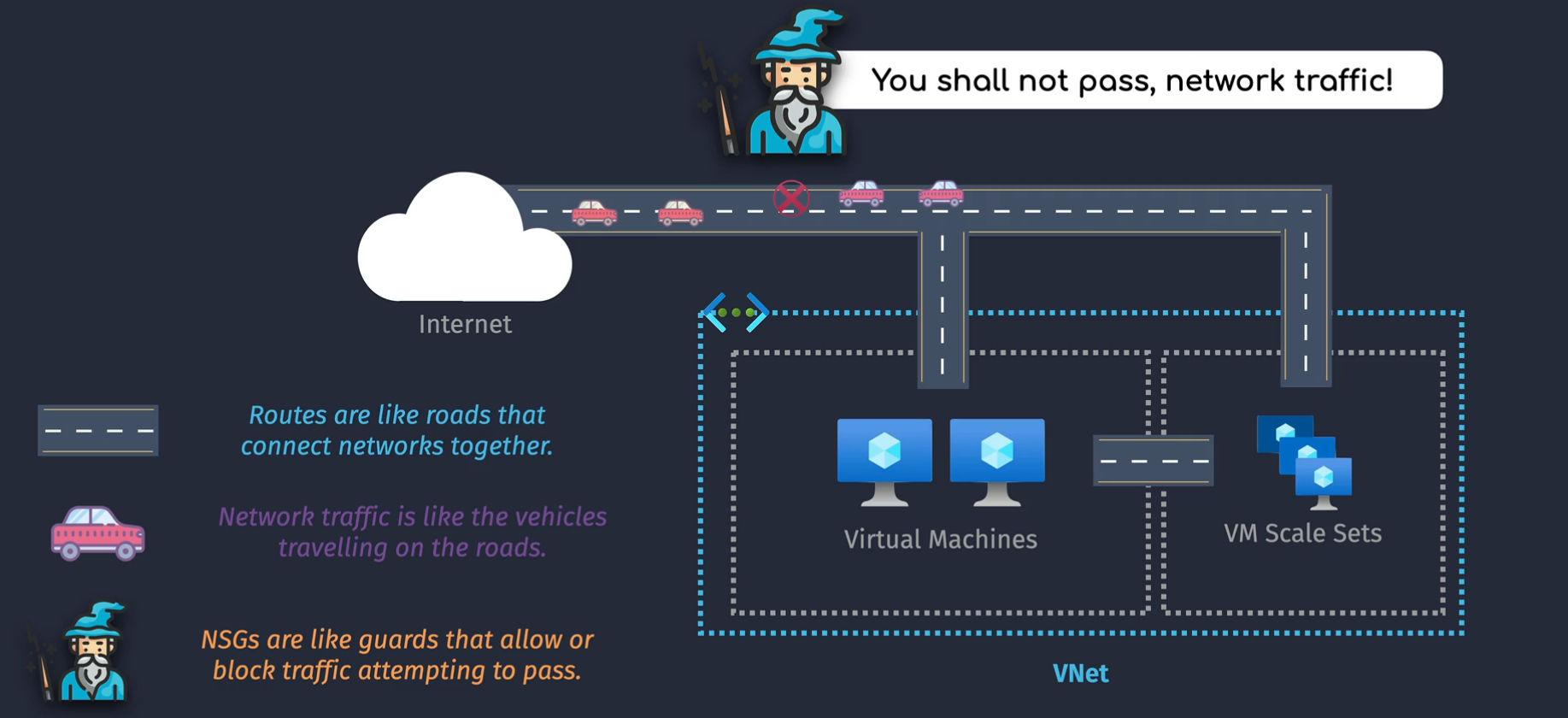 Act like a guard on the "roads" of the network
Act like a guard on the "roads" of the network
- list of outbound and inbound traffic allowed or denied.
- assigned at the subnet or NIC level or both
- each rule defines the type of traffic allowed or denied into the destination of the NSG.
Set up by priority - lower number is a higher priority. Once the traffic matches a rule, the rest of the rules are dropped. There are 3 default rules that cannot be deleted.
Deny by default - everything is blocked except what you allow.
Inbound traffic: Subnets take priority over NICs when assigning NSGs. If your NSG on the subnet blocks RDP, creating an NSG and attaching it to a NIC is not going to allow RDP to that machine that the NIC is attached to.
Outbound traffic: NICs take priority over the subnet NSGs
NSGs attached at the subnet level act as if they are attached to the NICs, so if you deny RDP on the subnet, you will not be able to RDP from one machine in the subnet to another inside of the subnet.
NSGs are stateful firewalls. If I let you out, I will also let you back in. -NSG guard
Demo - Create an NSG
Microsoft has made it a bit more secure. You need to define inbound RDP and SSH connections by default now.
- Create VM
- Create Public IP on that VM
- Create NSG with 3389 allowed to the subnet that the VM resides in
- Connect to VM via public IP.
Augmented Security Rules
Azure services can be used in rules by using Service Tags. Application security groups can also be used. These group VMs together under a common grouping.
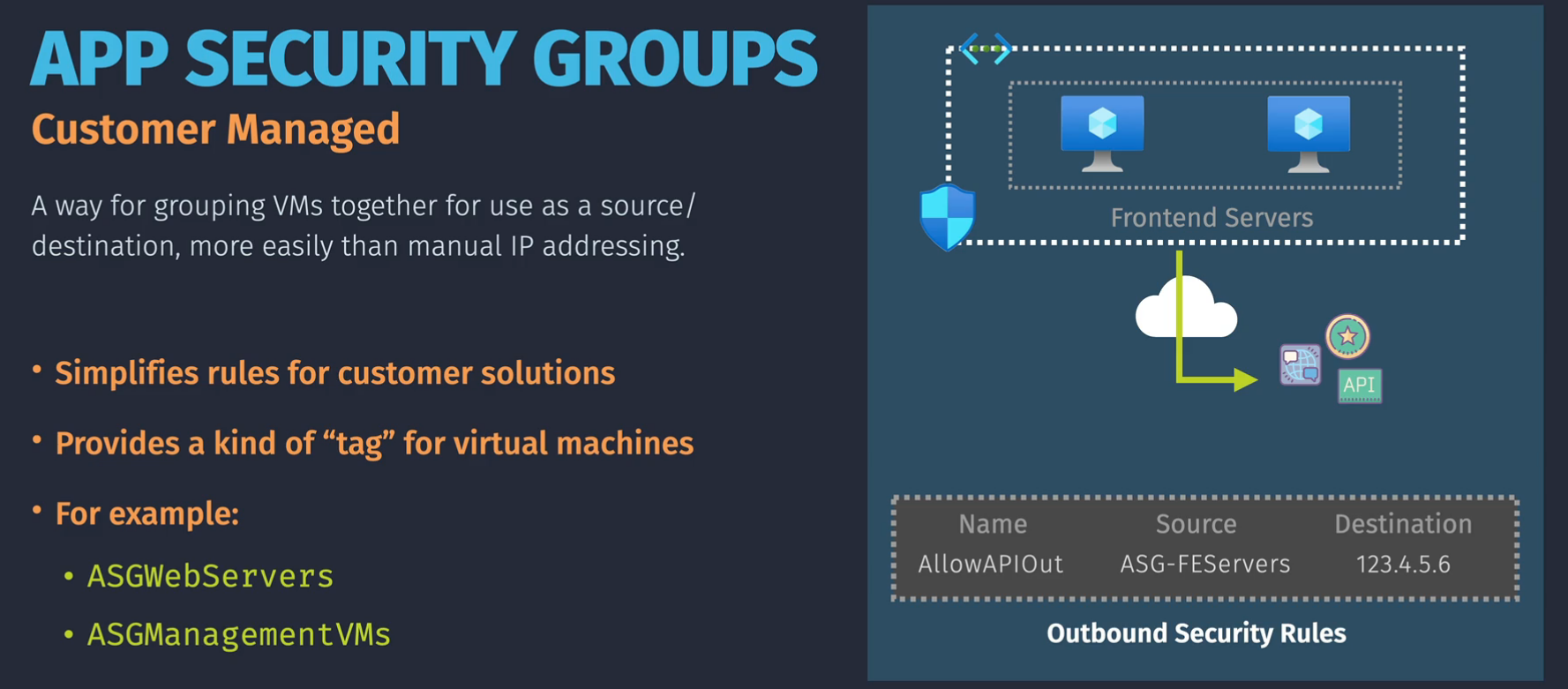
- All VMs in an ASG must be from the same vnet
- All source and destinations must be from the same vnet
- cannot create custom service tags
Demo - Use ASGs and Service Tags
- Create some VMs
- Create an ASG
- Add the VMs to the ASG
- Create an NSG
- Add the Service Tags to the Azure Resource Manager and block those from the NSG
- Create an RDP to the ASG on the NSG
- Confirm you can RDP to the servers and log into Azure but Azure #fails.
Case Study - Networking